

As AI-generated media, deepfakes, and content manipulation become more sophisticated, the need for authentic, verifiable digital content has never been greater. C2PA (Coalition for Content Provenance and Authenticity) offers a solution by allowing cryptographic signatures and metadata to be embedded in media files, proving their origin and integrity.
EZDRM, a leader in digital rights management, approached Qualabs with a clear goal: to develop an implementation framework that showcases live video signing using C2PA. The solution needed to be ready for one of the biggest video technology events of the year, where it would demonstrate how real-time content authentication could work in practice.
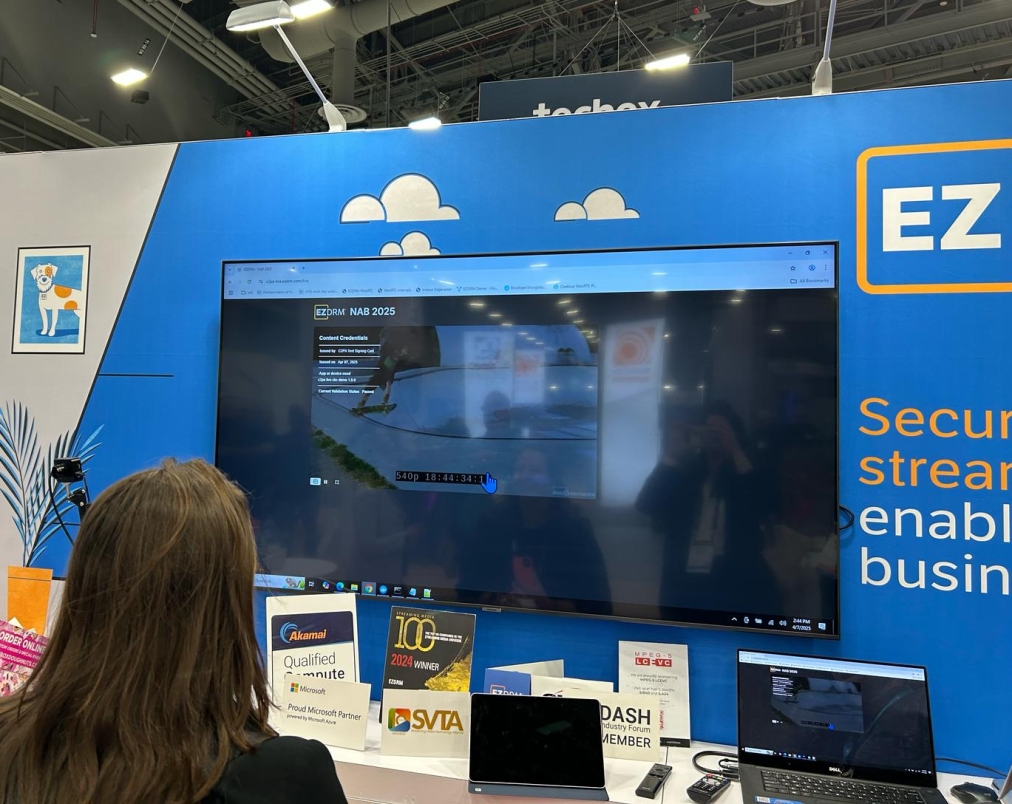
The project aimed to implement dynamic C2PA signing across multiple media formats, including images and VOD. However, the immediate priority was building a live video signing solution to showcase at the industry event.
The key challenges were:
Since no prior solutions existed for real-time C2PA signing in live streaming, the team had to define the entire technical architecture and execution strategy from scratch.
1. Uncovering Live‑Signing Requirements
We began by defining what a live C2PA signing workflow would require. Early workshops with streaming engineers showed that sidecar manifests conflicted with existing CDN and player setups.
Prototyping confirmed that the most effective solution was to inject metadata directly into the stream using a custom uuid box — preserving segment payloads and ensuring playback compatibility.
2. Iterating Chain‑Based Integrity
We experimented with chaining system to link each segment’s hash to its predecessor. Testing helped us balance two key factors:
• Security vs. recovery: Longer chains improve tamper resistance but increase recovery time if a segment is lost.
• Anchor cadence: Resetting the IV every 10 segments offered better recovery but required tuning with live traffic.
We also tackled a major challenge in ABR streams: switching renditions breaks the chain unless hashes are aligned. This led us to refine both chaining logic and manifest strategies.
3. Validating in the Player Environment
We built a lightweight validator inside a reference player, which uncovered performance issues — signature checks and hash recomputation added CPU and memory overhead.
• Optimization: We improved performance by caching public-key operations and reusing hash contexts.
• Result: Real-time validation ran smoothly on 1080p and 720p streams, without playback disruption.
4. Documenting Specification Gaps
During development, we found areas where the C2PA spec lacked clarity for live video:
• Key derivation: No defined method for per-segment keys.
• IV management: Unclear best practices for resets.
• ABR consistency: No guidance for chaining across multi-bitrate variants.
These gaps became the basis for our draft proposals to the C2PA working group.
The team delivered a production-ready signing proxy capable of performing all critical steps in the live signing workflow:
Fragment ingestion, it processes each live fMP4 segment. Hashing, executes chaining algorithm with anchor-point resets. Signing, uses the C2PA toolchain to serialize and sign each hash. Embedding, injects both the signature and hash into the segment’s uuid box.
On the client side, our validator library integrates directly into existing players. It reads the embedded metadata, replays the CBC chain, and verifies signatures in real time, triggering tamper alerts without interrupting playback
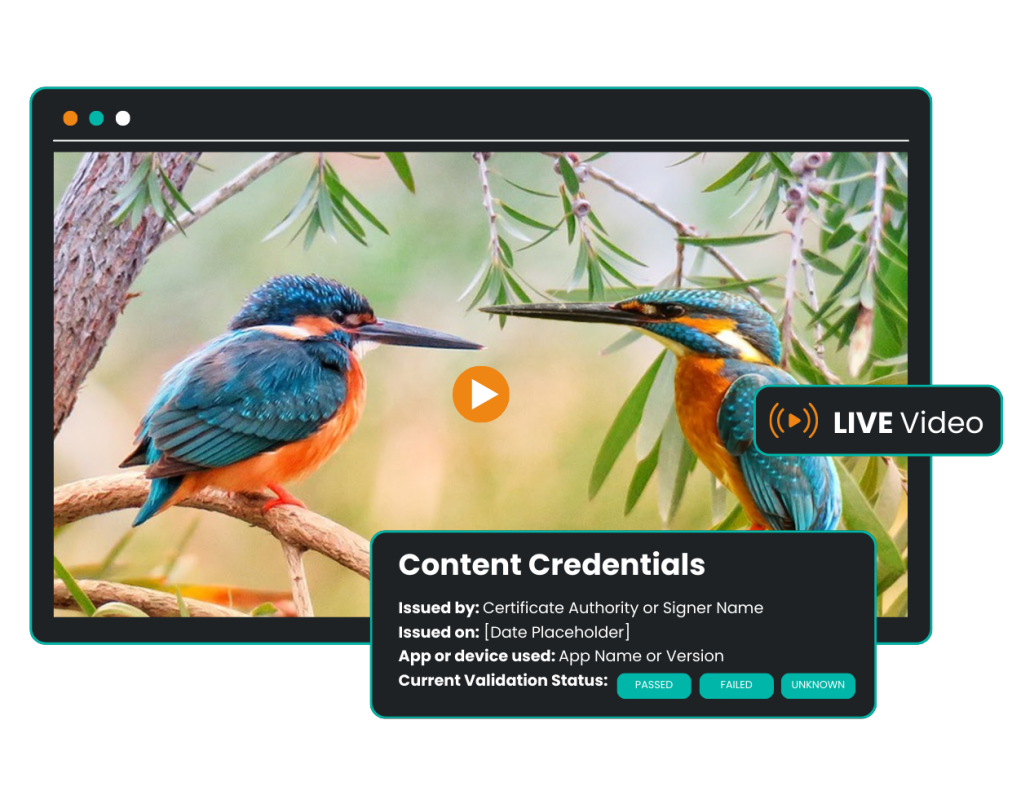
With the core pipeline complete, we’re now packaging the system as a reference implementation. Current efforts focus on: ABR support, synchronizing hash chains across multiple renditions. Spec standardization, collaborating with C2PA to define best practices for key-IV derivation, anchor cadence, and multi-bitrate chaining.
The proof of concept was successfully delivered on time and demonstrated live C2PA video signing in a live setting at the client’s target industry event. This high-impact demo proved that provenance and authenticity can be maintained — even in dynamic live streaming workflows.
• Sub-second processing: Each pull → hash → sign → embed cycle completed in under 500 ms, well within live-stream buffering budgets.
• Seamless playback: Embedding signatures via a uuid box had no negative impact on codec compatibility or buffer health.
• Real-time validation: Player-side validators confirmed signature integrity on 1080p and 720p streams with minimal CPU overhead.
• Self-validating segments: Tampered, dropped, or reordered segments were detected immediately through chained hash verification.
Beyond its technical success, this implementation framework paved the way for broader C2PA adoption across live and on-demand content. It also provided key insights into performance, metadata handling, and secure media processing.
The collaborative effort contributed directly to the refinement of the C2PA specification — highlighting gaps in key management, IV resets, and ABR chaining — and informed proposals to the working group.
By delivering this solution, Qualabs helped EZDRM with their strategic positioning around products that leverage C2PA deployment at scale, reinforcing their role as an innovator in secure media workflows.